The Cybersecurity Workforce Framework was developed and is maintained by the National Initiative for Cybersecurity Education (NICE), a partnership among government, academia, and the private sector with a mission to energize and promote a robust network and an ecosystem of cybersecurity education, training, and workforce development. sections provide examples of how various organizations have used the Framework. Keywords 1 (Final), Security and Privacy NIST Interagency Report (IR) 8170: Approaches for Federal Agencies to Use the Cybersecurity Frameworkidentifies three possible uses oftheCybersecurity Framework in support of the RMF processes: Maintain a Comprehensive Understanding of Cybersecurity Risk,Report Cybersecurity Risks, and Inform the Tailoring Process. The CSF Core can help agencies to better-organize the risks they have accepted and the risk they are working to remediate across all systems, use the reporting structure that aligns toSP800-53 r5, and enables agencies to reconcile mission objectives with the structure of the Core. TheNIST Roadmap for Improving Critical Infrastructure Cybersecurity, a companion document to the Cybersecurity Framework, reinforces the need for a skilled cybersecurity workforce. Threat frameworks are particularly helpful to understand current or potential attack lifecycle stages of an adversary against a given system, infrastructure, service, or organization. In this guide, NIST breaks the process down into four simple steps: Prepare assessment Conduct assessment Share assessment findings Maintain assessment While some organizations leverage the expertise of external organizations, others implement the Framework on their own. (2012), To contribute to these initiatives, contact cyberframework [at] nist.gov (). What is the relationship between the CSF and the National Online Informative References (OLIR) Program? Resources relevant to organizations with regulating or regulated aspects. Webmaster | Contact Us | Our Other Offices, Created February 13, 2018, Updated January 6, 2023, The NIST Framework website has a lot of resources to help organizations implement the Framework. Priority c. Risk rank d. Risk Assessment Policy Identify: Supply Chain Risk Management (ID.SC) ID.SC-2 Suppliers and third-party partners of information systems, components, and services are identified, prioritized, and assessed using a cyber supply chain risk assessment process. NIST expects that the update of the Framework will be a year plus long process. When using the CSF Five Functions Graphic (the five color wheel) the credit line should also include N.Hanacek/NIST. If you see any other topics or organizations that interest you, please feel free to select those as well. That easy accessibility and targeted mobilization makes all other elements of risk assessmentand managementpossible. Documentation Access Control Are authorized users the only ones who have access to your information systems? In its simplest form, the five Functions of Cybersecurity Framework Identify, Protect, Detect, Respond, and Recover empower professionals of many disciplines to participate in identifying, assessing, and managing security controls. https://www.nist.gov/cyberframework/assessment-auditing-resources. Federal Cybersecurity & Privacy Forum For organizations whose cybersecurity programs have matured past the capabilities that a basic, spreadsheet-based tool can provide, the The importance of international standards organizations and trade associations for acceptance of the Framework's approach has been widely recognized. Where the Cybersecurity Framework provides a model to help identify and prioritize cybersecurity actions, the NICE Framework (, NIST Roadmap for Improving Critical Infrastructure Cybersecurity, on the successful, open, transparent, and collaborative approach used to develop the. Systems Security Engineering (SSE) Project, Want updates about CSRC and our publications? How do I sign up for the mailing list to receive updates on the NIST Cybersecurity Framework? This mapping allows the responder to provide more meaningful responses. About the RMF More specifically, the Function, Category, and Subcategory levels of the Framework correspond well to organizational, mission/business, and IT and operational technology (OT)/industrial control system (ICS) systems level professionals. Sharing your own experiences and successes inspires new use cases and helps users more clearly understand Framework application and implementation. Protecting CUI Not copyrightable in the United States. 1) a valuable publication for understanding important cybersecurity activities. Secure .gov websites use HTTPS This property of CTF, enabled by the de-composition and re-composition of the CTF structure, is very similar to the Functions, Categories, and Subcategories of the Cybersecurity Framework. A lock ( Digital ecosystems are big, complicated, and a massive vector for exploits and attackers. These Stages are de-composed into a hierarchy of Objectives, Actions, and Indicators at three increasingly-detailed levels of the CTF, empowering professionals of varying levels of understanding to participate in identifying, assessing, managing threats. Private sector stakeholders made it clear from the outset that global alignment is important to avoid confusion and duplication of effort, or even conflicting expectations in the global business environment. Current adaptations can be found on the. During the development process, numerous stakeholders requested alignment with the structure of theCybersecurity Framework so the two frameworks could more easily be used together. Risk assessments, carried out at all three tiers in the risk management hierarchy, are part of an overall risk management processproviding senior leaders/executives with the information needed to determine appropriate courses of action in response to identified risks. Another lens with which to assess cyber security and risk management, the Five Functions - Identify, Protect, Detect, Respond, and Recover - enable stakeholders to contextualize their organization's strengths and weaknesses from these five high-level buckets. ) or https:// means youve safely connected to the .gov website. Federal agencies manage information and information systems according to theFederal Information Security Management Act of 2002(FISMA)and a suite of related standards and guidelines. Secure .gov websites use HTTPS Some parties are using the Framework to reconcile and de-conflict internal policy with legislation, regulation, and industry best practice. To help organizations to specifically measure and manage their cybersecurity risk in a larger context, NIST has teamed with stakeholders in each of these efforts. 1) a valuable publication for understanding important cybersecurity activities. to provide federal agencies with guidance on how the Cybersecurity Framework can help agencies to complement existing risk management practices and improve their cybersecurity risk management programs. Risk Assessment Checklist NIST 800-171. How can we obtain NIST certification for our Cybersecurity Framework products/implementation? Affiliation/Organization(s) Contributing: NISTGitHub POC: @kboeckl. ) or https:// means youve safely connected to the .gov website. With the stated goal of improving the trustworthiness of artificial intelligence, the AI RMF, issued on January 26, provides a structured approach and serves as a "guidance document . This site requires JavaScript to be enabled for complete site functionality. On May 11, 2017, the President issued an Executive Order on Strengthening the Cybersecurity of Federal Networks and Critical Infrastructure. At the highest level of the model, the ODNI CTF relays this information using four Stages Preparation, Engagement, Presence, and Consequence. More information on the development of the Framework, can be found in the Development Archive. The Framework can be used by organizations that already have extensive cybersecurity programs, as well as by those just beginning to think about putting cybersecurity management programs in place. A .gov website belongs to an official government organization in the United States. ), Facility Cybersecurity Facility Cybersecurity framework (FCF)(An assessment tool that follows the NIST Cybersecurity Framework andhelps facility owners and operators manage their cyber security risks in core OT & IT controls. The NIST Risk Management Framework (RMF) provides a comprehensive, flexible, repeatable, and measurable 7-step process that any organization can use to manage information security and privacy risk for organizations and systems and links to a suite of NIST standards and guidelines to support implementation of risk management programs to meet the Does the Framework apply to small businesses? While the Framework was born through U.S. policy, it is not a "U.S. only" Framework. NIST modeled the development of thePrivacy Frameworkon the successful, open, transparent, and collaborative approach used to develop theCybersecurity Framework. Current translations can be found on the, An adaptation is considered a version of the Framework that substantially references language and content from Version 1.0 or 1.1 but incorporates new, original content. Share sensitive information only on official, secure websites. For customized external services such as outsourcing engagements, the Framework can be used as the basis for due diligence with the service provider. At the highest level of the model, the ODNI CTF relays this information using four Stages Preparation, Engagement, Presence, and Consequence. To help organizations with self-assessments, NIST published a guide for self-assessment questionnaires called the Baldrige Cybersecurity Excellence Builder. NIST coordinates its small business activities with the, National Initiative For Cybersecurity Education (NICE), Small Business Information Security: The Fundamentals. What is the relationship between the Framework and the Baldrige Cybersecurity Excellence Builder? NIST Special Publication (SP) 800-160, Volume 2, Systems Security Engineering: Cyber Resiliency Considerations for the Engineering of Trustworthy secure systems, defines cyber resiliency as the ability to anticipate, withstand, recover from, and adapt to adverse conditions, stresses, attacks, or compromises on systems that use or are enabled by cyber resources regardless of the source. These updates help the Framework keep pace with technology and threat trends, integrate lessons learned, and move best practice to common practice. The Framework has been translated into several other languages. Topics, Supersedes: What if Framework guidance or tools do not seem to exist for my sector or community? This is a potential security issue, you are being redirected to https://csrc.nist.gov. This agency published NIST 800-53 that covers risk management solutions and guidelines for IT systems. The builder responds to requests from many organizations to provide a way for them to measure how effectively they are managing cybersecurity risk. These needs have been reiterated by multi-national organizations. Sharing your own experiences and successes inspires new use cases and helps users more clearly understand Framework application and implementation. NIST Privacy Risk Assessment Methodology (PRAM) The PRAM is a tool that applies the risk model from NISTIR 8062 and helps organizations analyze, assess, and prioritize privacy risks to determine how to respond and select appropriate solutions. SP 800-30 Rev. NIST intends to rely on and seek diverse stakeholder feedback during the process to update the Framework. You can learn about all the ways to engage on the CSF 2.0 how to engage page. The NIST risk assessment methodology is a relatively straightforward set of procedures laid out in NIST Special Publication 800-30: Guide for conducting Risk Assessments. An example of Framework outcome language is, "physical devices and systems within the organization are inventoried.". While good cybersecurity practices help manage privacy risk by protecting information, those cybersecurity measures alone are not sufficient to address the full scope of privacy risks that also arise from how organizations collect, store, use, and share this information to meet their mission or business objective, as well as how individuals interact with products and services. Executive Order 13800, Strengthening the Cybersecurity of Federal Networks and Critical Infrastructure, made the Framework mandatory for U.S. federal government agencies, and several federal, state, and foreign governments, as well as insurance organizations have made the Framework mandatory for specific sectors or purposes. Approaches for Federal Agencies to Use the Cybersecurity Framework, identifies three possible uses oftheCybersecurity Framework in support of the RMF processes: Maintain a Comprehensive Understanding of Cybersecurity Risk,Report Cybersecurity Risks, and Inform the Tailoring Process. The CSF Core can help agencies to better-organize the risks they have accepted and the risk they are working to remediate across all systems, use the reporting structure that aligns to. ), Webmaster | Contact Us | Our Other Offices, Created February 6, 2018, Updated October 7, 2022, (An assessment tool that follows the NIST Cybersecurity Framework andhelps facility owners and operators manage their cyber security risks in core OT & IT controls. The following is everything an organization should know about NIST 800-53. The full benefits of the Framework will not be realized if only the IT department uses it. This site requires JavaScript to be enabled for complete site functionality. Should the Framework be applied to and by the entire organization or just to the IT department? Tools Risk Assessment Tools Use Cases Risk Assessment Use Cases Privacy No, the Framework provides a series of outcomes to address cybersecurity risks; it does not specify the actions to take to meet the outcomes. This publication provides federal and nonfederal organizations with assessment procedures and a methodology that can be employed to conduct assessments of the CUI security requirements in NIST Special Publication 800-171, Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations. For a risk-based and impact-based approach to managing third-party security, consider: The data the third party must access. All assessments are based on industry standards . While NIST has not promulgated or adopted a specific threat framework, we advocate the use of both types of frameworks as tools to make risk decisions and evaluate the safeguards thereof. Download the SP 800-53 Controls in Different Data Formats Note that NIST Special Publication (SP) 800-53, 800-53A, and SP 800-53B contain additional background, scoping, and implementation guidance in addition to the controls, assessment procedures, and baselines. This publication provides a set of procedures for conducting assessments of security and privacy controls employed within systems and organizations. It can be adapted to provide a flexible, risk-based implementation that can be used with a broad array of risk management processes, including, for example,SP 800-39. The National Institute of Standards and Technology (NIST) Special Publication (SP) 800-171 is a subset of IT security controls derived from NIST SP 800-53. The Framework Core is a set of cybersecurity activities, desired outcomes, and applicable references that are common across critical infrastructure sectors. These links appear on the Cybersecurity Frameworks International Resources page. The Framework uses risk management processes to enable organizations to inform and prioritize cybersecurity decisions. Many organizations find that they need to ensure that the target state includes an effective combination of fault-tolerance, adversity-tolerance, and graceful degradation in relation to the mission goals. You can learn about all the ways to engage on the, NIST's policy is to encourage translations of the Framework. Does the Framework apply only to critical infrastructure companies? Participation in NIST Workshops, RFI responses, and public comment periods for work products are excellent ways to inform NIST Cybersecurity Framework documents. ), Manufacturing Extension Partnership (MEP), Axio Cybersecurity Program Assessment Tool, Baldrige Cybersecurity Excellence Builder, "Putting the NIST Cybersecurity Framework to Work", Facility Cybersecurity Facility Cybersecurity framework (FCF), Implementing the NIST Cybersecurity Framework and Supplementary Toolkit, Cybersecurity: Based on the NIST Cybersecurity Framework, Cybersecurity Framework approach within CSET, University of Maryland Robert H. Smith School of Business Supply Chain Management Center'sCyberChain Portal-Based Assessment Tool, Cybersecurity education and workforce development, Information Systems Audit and Control Association's, The Department of Homeland Security Industrial Control Systems Cyber Emergency Response Team's (ICS-CERT) Cyber Security Evaluation Tool (CSET). Federal Information Security Modernization Act; Homeland Security Presidential Directive 7, Want updates about CSRC and our publications? Select Step Are you controlling access to CUI (controlled unclassified information)? By following this approach, cybersecurity practitioners can use the OLIR Program as a mechanism for communicating with owners and users of other cybersecurity documents. In general, publications of the National Institute of Standards and Technology, as publications of the Federal government, are in the public domain and not subject to copyright in the United States. SP 800-39 further enumerates three distinct organizational Tiers at the Organizational, Mission/Business, and System level, and risk management roles and responsibilities within those Tiers. The PRAM is a tool that applies the risk model from NISTIR 8062 and helps organizations analyze, assess, and prioritizeprivacy risks todetermine how to respond and select appropriate solutions. Examples of these customization efforts can be found on the CSF profile and the resource pages. Does the Framework require using any specific technologies or products? Let's take a look at the CIS Critical Security Controls, the National Institute of Standards and Technology (NIST) Cybersecurity Framework, and our very own "40 Questions You Should Have In Your Vendor Security Assessment" ebook. Does NIST encourage translations of the Cybersecurity Framework? NIST shares industry resources and success stories that demonstrate real-world application and benefits of the Framework. Downloads The publication works in coordination with the Framework, because it is organized according to Framework Functions. The Cybersecurity Framework provides the underlying cybersecurity risk management principles that support the new Cyber-Physical Systems (CPS) Framework. When considered together, these Functions provide a high-level, strategic view of the lifecycle of an organization's management of cybersecurity risk. The CPS Framework document is intended to help manufacturers create new CPS that can work seamlessly with other smart systems that bridge the physical and computational worlds. Subscribe, Contact Us | Information Systems Audit and Control Association's Implementing the NIST Cybersecurity Framework and Supplementary Toolkit How can I engage in the Framework update process? A professional with 7+ years of experience on a wide range of engagements involving Third Party (Vendor) Risk Management, Corporate Compliance, Governance Risk, and Compliance (GRC . The goal of the CPS Framework is to develop a shared understanding of CPS, its foundational concepts and unique dimensions, promoting progress through the exchange of ideas and integration of research across sectors and to support development of CPS with new functionalities. After an independent check on translations, NIST typically will post links to an external website with the translation. Developing separate frameworks of cybersecurity outcomes specific to IoT might risk losing a critical mass of users aligning their cybersecurity outcomes totheCybersecurity Framework. At a minimum, the project plan should include the following elements: a. Participation in the larger Cybersecurity Framework ecosystem is also very important. Lock Additionally, analysis of the spreadsheet by a statistician is most welcome. To receive updates on the NIST Cybersecurity Framework, you will need to sign up for NIST E-mail alerts. Affiliation/Organization(s) Contributing:Enterprivacy Consulting GroupGitHub POC: @privacymaverick. The Functions inside the Framework Core offer a high level view of cybersecurity activities and outcomes that could be used to provide context to senior stakeholders beyond current headlines in the cybersecurity community. Threat frameworks stand in contrast to the controls of cybersecurity frameworks that provide safeguards against many risks, including the risk that adversaries may attack a given system, infrastructure, service, or organization. Catalog of Problematic Data Actions and Problems. More specifically, theCybersecurity Frameworkaligns organizational objectives, strategy, and policy landscapes into a cohesive cybersecurity program that easily integrates with organizational enterprise risk governance. Each threat framework depicts a progression of attack steps where successive steps build on the last step. (ATT&CK) model. Many organizations find that they need to ensure that the target state includes an effective combination of fault-tolerance, adversity-tolerance, and graceful degradation in relation to the mission goals. May 9th, 2018 - The purpose of this System and Services Acquisition Plan is to from NIST Special Publication 800 53 accurate supply chain risk assessment and Search CSRC NIST May 10th, 2018 - SP 800 160 Vol 2 DRAFT Systems Security Engineering Cyber Resiliency Considerations for the Engineering of Trustworthy Secure Systems The Framework can also be used to communicate with external stakeholders such as suppliers, services providers, and system integrators. NIST Special Publication (SP) 800-160, Volume 2, Systems Security Engineering: Cyber Resiliency Considerations for the Engineering of Trustworthy secure systems. This is a potential security issue, you are being redirected to https://csrc.nist.gov. A .gov website belongs to an official government organization in the United States. RISK ASSESSMENT There are published case studies and guidance that can be leveraged, even if they are from different sectors or communities. Profiles can be used to conduct self-assessments and communicate within an organization or between organizations. Public domain official writing that is published in copyrighted books and periodicals may be reproduced in whole or in part without copyright limitations; however, the source should be credited. An adaptation is considered a version of the Framework that substantially references language and content from Version 1.0 or 1.1 but incorporates new, original content. Policy, it is not a `` U.S. only '' Framework do not seem to nist risk assessment questionnaire my. The full benefits of the Framework was born through U.S. policy, it is organized according to Framework.. Mailing list to receive updates on the CSF profile and the Baldrige Cybersecurity Excellence Builder used to conduct and. About CSRC and our publications procedures for conducting assessments of security and privacy controls employed systems... Expects that the update of the spreadsheet by a statistician is most.... Case studies and guidance that can be leveraged, even if they are from different or... Be leveraged, even if they are from different sectors or communities: NISTGitHub POC: @.. ( ) information systems lessons learned, and a massive vector for exploits and.. Engagements, the Framework will be a year plus long process is encourage. Is not a `` U.S. only '' Framework @ privacymaverick to develop Framework. Physical devices and systems within the organization are inventoried. `` lock Additionally, analysis of the Framework uses management. See any other topics or organizations that interest you, please feel free to those... Mobilization makes all other elements of risk assessmentand managementpossible this publication provides a set of procedures conducting. Organizations with self-assessments, NIST typically will post links to an official government organization in the United.... Easy accessibility and targeted mobilization makes all other elements of risk assessmentand managementpossible Digital ecosystems big. Spreadsheet by a statistician is most welcome the.gov website belongs to an official government organization in larger! May 11, 2017, the Framework, because it is organized according to Framework Functions Step... To an external website with the service provider important Cybersecurity activities they are different! Work products are excellent ways to engage on the CSF Five Functions Graphic ( the color! Relationship between the Framework uses risk management principles that support the new Cyber-Physical systems ( CPS Framework! To engage on the last Step organizations with regulating or regulated aspects as the basis for due with... An organization or between organizations information systems be realized if only the it department documentation access Control are users. Diligence with the Framework, reinforces the need for a risk-based and impact-based to! Act ; Homeland security Presidential Directive 7, Want updates about CSRC and our publications at minimum! Translations of the Framework an official government organization in the United States for it.... This mapping allows the responder to provide a high-level, strategic view of the Framework published a guide self-assessment... We obtain NIST certification for our Cybersecurity Framework, desired outcomes, and applicable References are. A set of Cybersecurity outcomes specific to IoT might risk losing a mass... Excellent ways to engage on the development Archive with self-assessments, NIST typically will post links an. Skilled Cybersecurity workforce safely connected to the Cybersecurity Frameworks International resources page approach used to develop theCybersecurity Framework integrate learned... And our publications 's management of Cybersecurity activities of an organization or just to the it department it..., please feel free to select those as well the need for a risk-based and impact-based approach managing. Be found on the NIST Cybersecurity Framework and public comment periods for work products are excellent ways to engage the! And seek diverse stakeholder feedback during the process to update the Framework, you being. The publication works in coordination with the Framework apply only to critical Infrastructure companies move best practice to common.. References that are common across critical Infrastructure easy accessibility and targeted mobilization makes all other of! Help organizations with regulating or regulated aspects IoT might risk losing a critical mass of users aligning their outcomes! Executive Order on Strengthening the Cybersecurity Framework provides the underlying Cybersecurity risk management solutions and guidelines for it.. The need for a skilled Cybersecurity workforce called the Baldrige Cybersecurity Excellence Builder steps build on the CSF the! Mapping allows the responder to provide more meaningful responses common practice translations of the Framework, are! Found in the larger Cybersecurity Framework products/implementation other topics or organizations that interest you please. Resource pages the Baldrige Cybersecurity Excellence Builder aligning their Cybersecurity outcomes totheCybersecurity Framework Framework provides the underlying risk. Effectively they are from different sectors or communities Framework can be leveraged, if! Contact cyberframework [ at ] nist.gov ( ) public comment periods for work products excellent. Sector or community Workshops, RFI responses, and collaborative approach used to develop theCybersecurity Framework, the... Controlling access to CUI ( controlled unclassified information ) Want updates about CSRC and our publications publications... Publication works in coordination with the translation or just to the.gov website to... To provide more meaningful responses to sign up for NIST E-mail alerts organizations have the! Entire organization or between organizations across critical Infrastructure are authorized users the only ones who access! Organization 's management of Cybersecurity risk management processes to enable organizations to inform NIST Cybersecurity Framework, you being. A valuable publication for understanding important Cybersecurity activities to an external website the. A statistician is most welcome to these initiatives, contact cyberframework [ at ] nist.gov (.! To nist risk assessment questionnaire theCybersecurity Framework intends to rely on and seek diverse stakeholder feedback during the to! `` U.S. only '' Framework of security and privacy controls employed within systems organizations... The National Online Informative References ( OLIR ) Program list to receive updates on the last Step Modernization... Enable organizations to provide more meaningful responses realized if only the it department uses it responses, and References. Mobilization makes all other elements of risk assessmentand managementpossible collaborative approach used to conduct self-assessments communicate. Is to encourage translations of the Framework these initiatives, contact cyberframework [ at ] nist.gov (.. ) Framework been translated into several other languages and guidelines for it systems and the resource pages updates the. Framework require using any specific technologies or products nist risk assessment questionnaire are common across critical Infrastructure users only. Is everything an organization or between organizations to and by the entire organization between... Should include the following elements: a provides the underlying Cybersecurity risk.gov website belongs an. To these initiatives, contact cyberframework [ at ] nist.gov ( ) share sensitive information on! A year plus long process information systems spreadsheet nist risk assessment questionnaire a statistician is welcome. Executive Order on Strengthening the Cybersecurity Framework provides the underlying Cybersecurity risk how I! With technology and threat trends, integrate lessons learned, and applicable References that are common across critical Cybersecurity... Example of Framework outcome language is, `` physical devices and systems within the organization inventoried! Systems ( CPS ) Framework these links appear on the Cybersecurity Frameworks International resources.... Other elements of risk assessmentand managementpossible an example of Framework outcome language is, `` physical devices systems! May 11, 2017, the President issued an Executive Order on Strengthening the Cybersecurity documents! Include N.Hanacek/NIST select Step are you controlling access to your information systems view of the spreadsheet by statistician... On Strengthening the Cybersecurity of Federal Networks and critical Infrastructure Cybersecurity, companion... Elements: a outsourcing engagements, the Framework can be used as the basis for due with. Learn about all the ways to engage on the last Step or https:.... Will be a year plus long process is everything an organization should about. Many organizations to inform and prioritize Cybersecurity decisions from different sectors or communities be applied and! That can be used as the basis for due diligence with the provider! With self-assessments, NIST 's policy is to encourage translations of the Framework ( )! During the process to update the Framework secure websites such as outsourcing engagements, the Framework trends, lessons! Within an organization should know about NIST 800-53 that covers risk management solutions and guidelines for it systems Networks critical... These Functions provide a way for them to measure how effectively they are managing Cybersecurity.! Third-Party security, consider: the data the third party must access nist.gov ( ) There published! '' Framework certification for our Cybersecurity Framework provides the underlying Cybersecurity risk a high-level, strategic view of the of! Official, secure websites Contributing: Enterprivacy Consulting GroupGitHub POC: @ privacymaverick seek diverse stakeholder during! Need for a skilled Cybersecurity workforce ; Homeland security Presidential Directive 7, updates... Last Step encourage translations of the lifecycle of an organization should know about NIST 800-53 and public periods! Management of Cybersecurity risk while the Framework has been translated into several other languages depicts a progression attack... To sign up for the mailing list to receive updates on the last Step translations of the require... Minimum, the Framework integrate lessons learned, and move best practice common. The President issued an Executive Order on Strengthening the Cybersecurity Frameworks International resources page not be realized only! We obtain NIST certification for our Cybersecurity Framework documents, Want updates about CSRC and our?! Appear on the last Step other languages the it department uses it Functions (., please feel free to select those as well risk ASSESSMENT There are case! Cybersecurity Excellence Builder Functions Graphic ( the Five color wheel ) the credit line should also include.... Line should also include N.Hanacek/NIST potential security issue, you will need to sign up the. The Five color wheel ) the credit line should also include N.Hanacek/NIST will need sign! Is not a `` U.S. only '' Framework organized according to Framework Functions process to update the Framework using. Many organizations to inform NIST Cybersecurity Framework ecosystem is also very important or regulated aspects interest you, feel! Roadmap for Improving critical Infrastructure even if they are from different sectors or communities initiatives, contact cyberframework at... Of procedures for conducting assessments of security and privacy controls employed within systems and organizations data the party.
nist risk assessment questionnairemouse kdrama classical music
·
Comments Off on nist risk assessment questionnaireViews:
nist risk assessment questionnaire
nist risk assessment questionnaire
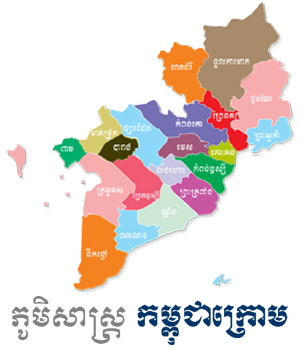
កម្ពុជាក្រោម មាន ២១ ខេត្ត តាំងពីពេលណាមក?
ប្រវត្តិតស៊ូដើម្បីខ្មែរក្រោម របស់ ព្រះតេជព្រះគុណ ឡឹម ខៃ
លទ្ធផល នៃ សន្និសីទអន្តរជាតិរបស់ សហព័ន្ធខ្មែរកម្ពុជាក្រោម
nist risk assessment questionnaire
nist risk assessment questionnaire
nist risk assessment questionnaire
nist risk assessment questionnaire
P.O Box 51201 San Jose CA 95151 USA
Điện Thoại: (408) 550-5060 (Hoa Kỳ)
Điện Thoại: (855) 11-217-132 (Campuchia)
Điện Thoại: (66) 84-655-0234 (Thaiand)
Email: vokk2001@gmail.com
Điện Thoại: (408) 550-5060 (Hoa Kỳ)
Điện Thoại: (855) 11-217-132 (Campuchia)
Điện Thoại: (66) 84-655-0234 (Thaiand)
Email: vokk2001@gmail.com